tl;dr If you run or own a website that doesn't enforce HTTPS, browsers will soon flag it as 'Not secure' (simply because it isn't). It's time to enforce HTTPS, "Let's Encrypt" is a free solution to request Digital Certificates if you are not planning to pay a fortune.
According to Firefox Telemetry, during 2016 the Web has gone from 39% of page loads using HTTPS every day to 49%, this is a huge step for humanity where soon the Web will be more encrypted than not. While many factors induced these results, "Let's Encrypt" had been a major player in democratizing HTTPS.
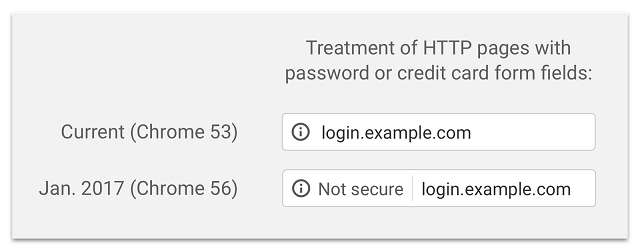
Browsers will start flagging your websites as 'Not secure' if HTTPS is not implemented
As an attempt to make webmasters vigilant about their visitors, major browsers (such as Google Chrome and Mozilla Firefox) will push them towards HTTPS, or else websites will be flagged as 'Not secure'.
Google Chrome will begin this behavior starting of version 56, which will be released on 31st of January 2017. On an end-user's side, the picture will look like this:
Let's Encrypt, if you don't want to pay for expensive certificates
"Let's Encrypt" is an initiative that aims to make Transport Layer Security (TLS) certificates available for free in an automated fashion. It is the result of a collective between two end-user privacy seekers ISRG (Internet Security Research Group) and EFF (Electronic Frontier Foundation) along with many other involved parties.
"Let's Encrypt" is compatible with different platforms and easy to manage, it provides:
- Free TLS Digital Certificates to encrypt transiting data from your website (SSL is very old, weak and depricated)
- Those TLS Digital Certificates are trusted by major browsers
- Certbot software (developed by EFF), runs on different platforms and does the main automated job to request, renew and install the certificates on the web server (automatic setup currently works on Apache and Nginx, manual setup is required on other platfroms)
- Certbot communicates with the Certificate Authority in order to acquire requested certificates
- More info about different platforms can be found under this link: https://certbot.eff.org/
Limitations:
- Certificates issued by "Let's Encrypt" are only valid for 90 days (but this shouldn't be an issue when Certbot is well configured for auto-generation)
- Wildcard certificates are not allowed (since it's easy to generate different Certificates for different sub-domains using Certbot)
- Certificates generated by "Let's Encrypt" do not validate the authenticity of the website being protected (since those TLS certificates do not go through an identity validation process).
If you think Let's Encrypt's installation is complicated and you don't want your website to be flagged as 'Not secure', you will fall under the below alternatives:
- Ask an experienced developer to implement "Let's Encrypt" on your website (don't ask for a free service)
- Cloudflare provides a free valid/trusted Certificate for encryption purposes too
- Purchase a valid certificate from your hosting provider (might cost as much as your hosting service, if not more)
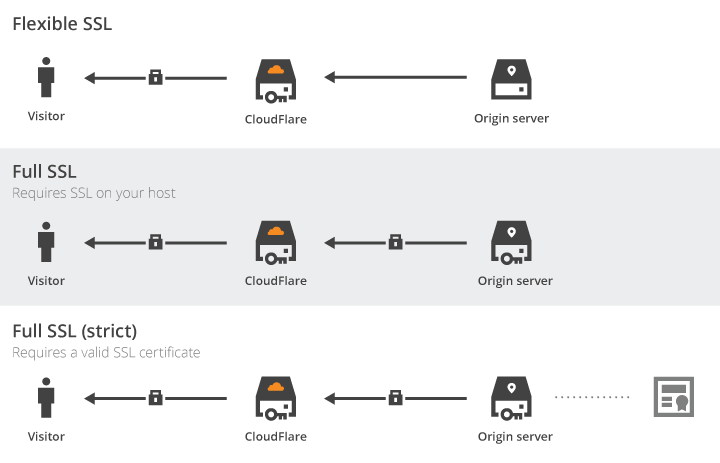
Regarding Cloudflare's free TLS Certificate
If you rely on Cloudflare as a middleware for HTTPS, the 'Flexible SSL' is not recommended, beware that it will only encrypt the connection between your vistors and Cloudflare but not between Cloudflare and your server. Leaving your administrative and visitors' transiting in clear text along with Session IDs. Use Full SSL if possible.
Forcing HTTPS does not resolve issues with mixed content, as browsers check the protocol of included resources before making a request. Cloudflare can automatically resolve some mixed-content links enabling 'Automatic HTTPS Rewrites' functionality.
Further considerations regarding HTTPS for a secured configuration
Enabling HTTPS is half-way towards its complete secured configuration, you still need to enforce and protect against HTTPS known attacks:
- After enabling HTTPS, always share your HTTPS versions with your friends and on social media
- SSL is deprecated and prone to many flaws, all SSL cipher suites should be disabled, keep TLS cipher suites instead
- Enforce HTTPS on all the sections on your websites (redirect all visited URLs to their HTTPS version)
- Set the session 'Secure flag' (this will prevent session cookies from being accidently transmitted on HTTP if accidently requested)
- Set the 'HTTPOnly flag' (this will disable JavaScript access to your session IDs, protecting them against Cross Site Scripting attacks)
- You will need to use only relative links (/path instead of www.domain.com/path) or hardcode all your URLs to https://www.domain.com/path



Leave a comment!